4 February 2014
A step by step guide in authenticating an external Tableau Server using SAML & AD FS 2.0 to achieve a seamless enterprise logon experience
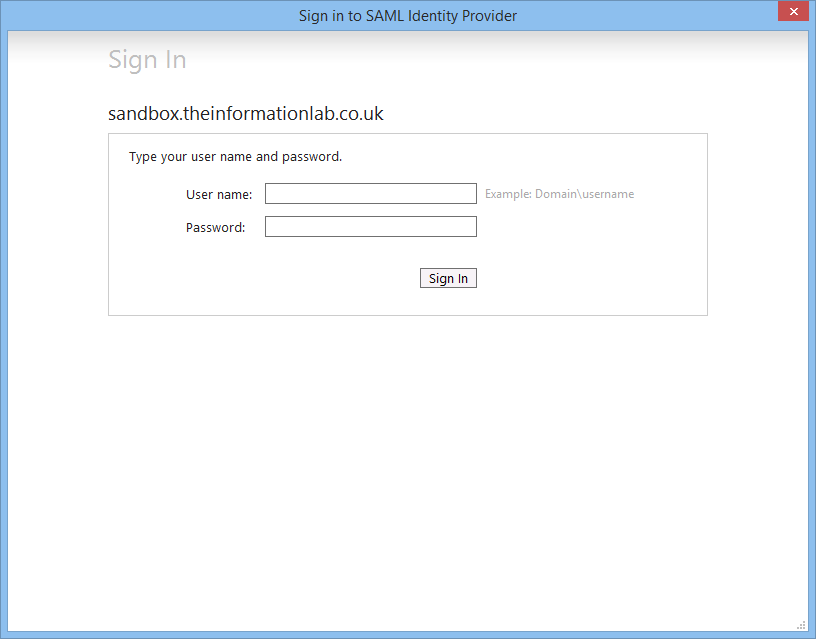
A client recently came to me with an interesting challenge. They wanted to embed Tableau Server dashboards in Salesforce (nicely demonstration by Ellie Fields) however instead of using Tableau Online they intended to install Tableau Server on an Amazon EC2 server alongside Amazon Redshift. Here's where it gets difficult, it needed to be a seamless single sign-on (SSO) experience from Salesforce to Tableau using enterprise Active Directory (AD) usernames and passwords.Clearly the authentication username-password challenge had to be done by active directory in order to keep usernames and passwords consistent, however until Tableau Server 8.1 our only option would have been to explore a custom trusted ticket authentication interface. With the introduction of SAML in Tableau 8.1 and Active Directory Federation Services (AD FS) 2.0 with Windows Server 2008 (as an update) & 2012 authentication could pass seamlessly from the active directory to Salesforce and then onto Tableau.So how do you go about configuring a Tableau Server, not situated anywhere near your enterprise domain, to work with active directory? Here's how....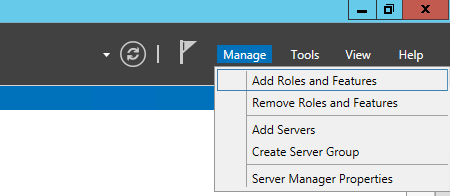
Prerequisites
It's assumed you have a working instance of Tableau Server & Windows active directory. The instructions will be based on Server 2012 however should also carry across into Server 2008 with the AD FS 2.0 update. You'll need a valid SSL certificate key pair for the AD FS server & Tableau Server, I'll point you in the right direction when it comes to it. It is also important that usernames configured on your Tableau Server match those on your active directory so if you haven't created an admin account on Tableau which matches the username of your own or test AD account I'd do that now.Getting a single AD FS instance up and running
I'm going to assume you don't have AD FS already installed & configured, if you do you can skim read this section, just make sure you save the FederationMetadata xml at the end.
- We're going to start in the top right of Server Manager -> Manage -> Add Roles and Features
- Follow the wizard to install Active Directory Federation Services (may require server restart)
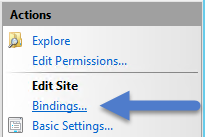 Edit the IIS Default Site bindings to assign the server certificate to the https protocol
Edit the IIS Default Site bindings to assign the server certificate to the https protocol- Start AD FS Management under Administrative Tools
- On the first run of AD FS Management you'll be presented with a wizard to configure the server. The questions are simple, at this point you're just looking to install a single instance of AD FS, not configure a farm (if you are configuring a farm why are you reading my step by step guide).
- When the wizard completes you should see a bunch of green ticks. You can then test that all's well by going to https://yourserver.yourdomain.com/FederationMetadata/2007-06/FederationMetadata.xml
- Save the FederationMetadata.xml file in a safe place, ideally transfer it now to your Tableau Server.
- Finally Tableau Server requires forms based authentication to serve logins via a web browser, Tableau Desktop and the Tableau Mobile app. In web.config found in the C:inetpubadfsls directory modify the tag order under <localAuthenticationTypes> so that <add name='Forms' page='FormsSignIn.aspx' /> appears first in the list. You can customise the login form by editing FormsSignIn.aspx in the same directory.
Configure Tableau Server for SAML authentication
While these steps are specific to AD FS SAML integration they can be translated to any SAML identity provider (IdP).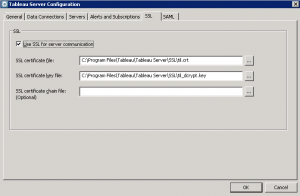 If you don't already have an SSL certificate for your Tableau Server follow these steps. Again you'll need to have the request signed by a fully configured enterprise or a third party CA. Don't forget the CN (common name) needs to be the fully qualified domain name of your Tableau Server as it'll be seen by the AD FS Server. e.g. tableau.theinformationlab.co.uk
If you don't already have an SSL certificate for your Tableau Server follow these steps. Again you'll need to have the request signed by a fully configured enterprise or a third party CA. Don't forget the CN (common name) needs to be the fully qualified domain name of your Tableau Server as it'll be seen by the AD FS Server. e.g. tableau.theinformationlab.co.uk- Open the Tableau Server configuration window and select the SSL tab.
- If SSL isn't already enabled tick the box and assign the certificate and key files created in the previous step
- Stop the Tableau Server (tabadmin stop), click OK on the configuration box, start the Tableau Server (tabadmin start) and check that the server is fully operational (tabadmin status --verbose) and is now accessed in a web browser via https instead of http
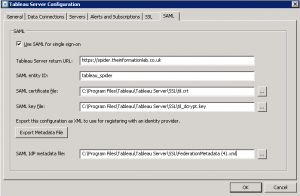 Open the Tableau configuration window again, this time selecting the SAML tab
Open the Tableau configuration window again, this time selecting the SAML tab- The Tableau Server return URL is the URL the user will be sent to after authenticating with SAML. It should be the URL of your Tableau Server beginning with https (to comply with AD FS endpoint requirements).
- You can give the server any SAML entity ID although it must be unique on your AD FS
- The SAML certificate and key files can be those used by your SSL config or they can be unique. Importantly the CN must match the return URL FQDN
- Once they're all set you can export your metadata file, this file needs to be copied across to your AD FS server
- Remember the FederationMetadata.xml file we saved earlier? Select it as the SAML IdP Metadata file
- Stop Tableau Server (tabadmin stop), click OK on the config screen, start the Tableau Server (tabadmin start)
Add Tableau to AD FS
- In AD FS Management, under Trust Relationships, right click on Relying Party Trust and Add Relying Party Trust
- In the second wizard screen select 'Import data about the relying party from a file' and browse to the exported Tableau SAML metadata xml file (the one you most recently copied)
- Click next...any error alerts at this point need to be rectified, the import should be seamless
- Give the config a friendly name e g. Tableau SAML and finish off the wizard
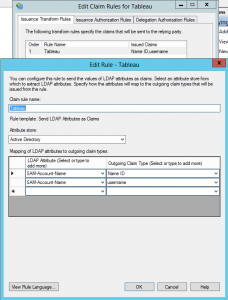 You should be asked to create some claim rules. If not right click on your new Relying Party Trust and select Edit Claim Rules.
You should be asked to create some claim rules. If not right click on your new Relying Party Trust and select Edit Claim Rules.- Under the Issuance Transform Rules tab cluck the Add Rule button
- For SAML authentication Tableau requires two attributes to be returned, Name ID and username, both of which can make use of the same AD attribute SAM-Account-Name
- Once configured all should be ready to go. Try logging in with a username already authorised on the Tableau Server (don't forget to use the AD password)
Troubleshooting
- Most errors are caused by poorly configured certificates. Make sure your certificates appear valid to both servers (during the FederationMetadata.XML or the Tableau SSL test you shouldn't receive any browser warnings about your certificates)
- If the AD FS accepts your login but doesn't forward you on to Tableau check the AD FS server logs. Some certificates require hash algorithm SHA-1 rather than SHA-256, this is set in the trust partner properties
- The following log files are useful (that can be found under ProgramData for installations on the C drive, Program Files for all other drives):
- tabadming.log (TableauTableau Serverlogs) - As the Tableau Server comes back online and 'Waiting for wgserver on 8000 to become ready' appears in the log look out for any 404 errors. This would indicate a problem with your certificates
- error.log (TableauTableau Serverdatatabsvclogshttpd) - Certificate errors referencing localhost:443 are OK however any other certificate errors would indicate a problem
- wgserver-#.log (TableauTableau Serverdatatabsvclogswgserver) - This is where you'll find SAML specific errors such as missing claim attributes